1. e-government made simple
5 Topics | 1 Quiz
2. e-health – How technology changes the way we manage our health
7 Topics | 1 Quiz
3. The basics about e-payment
5 Topics | 1 Quiz
4. e-leisure: Be your own tour operator!
5 Topics | 1 Quiz
5. e-participation. Raise Your Digital Voice!
5 Topics | 1 Quiz
How to protect yourself against scams?
When it comes to online fraud and cyber security, there is some specific vocabulary that you should be familiar with:
- Identity theft: Stealing someone’s identity online, usually by phishing when they provide personal information like bank account details.
- Phishing is an attempt to trick people into visiting malicious websites by sending emails or other messages that pretend to come from banks or online shops. The emails have links that take people to fake sites set up to look like the real thing, where passwords and account details can be stolen.
- Spam: Originally, spam was an email message sent to many people without their consent, usually promoting a product or service, also known as Unsolicited Commercial Email (UCE) or junk email. Now spam is not limited to email. Spam comments appear on blogs, social networking sites and many other places on the net.
- Malware: Short for ‘malicious software’. Here we can distinguish several types of it:
- Virus – a program that infects/damages your computer. Usually downloaded and installed from the Internet by mistake.
- Worm – a malicious program that replicates itself and sends copies to other computers via the network. They usually can be hidden in a mail attachment.
- Spyware – malware that steals your personal information.
- Adware – software that automatically displays/plays or downloads unwanted advertisements.
- Trojan horse – a destructive program that pretends to be useful but, once installed, damages your computer or exposes you to hackers.
- Pharming: Trying to steal someone’s information via a spoof/fake website, e.g. a fake PayPal site.
- Firewall: a software program or piece of hardware that helps screen out hackers, viruses, and worms that try to reach your computer over the Internet.
- Cookie: a small file sent to a web browser by a server and stored on the user’s computer. The server can then read it every time the user revisits the same website, and is used to keep track of personal preferences, shopping choices and other information.
- 2FA (Two-Factor Authentication): this is a security process in which users provide two different authentication factors to verify themselves. It adds an additional layer of security to the authentication process (which is usually a password) by making it harder for attackers to gain access to a person’s devices or online accounts because, even if the victim’s password is hacked, a password alone is not enough to pass the authentication check.
- VPN: means “Virtual Private Network” and describes the opportunity to establish a secure connection when using public networks. VPNs encrypt your Internet traffic and disguise your online identity. This makes it difficult for third parties to track your online activities and steal data.
First of all, whenever you are surfing on the Internet, practise all those general cyber security habits (those we have seen in the E-literacy unit) like:
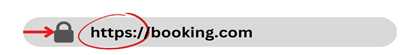 Check that the website is secure before paying for any service or providing your card details: HTTPS, a padlock and no spelling mistakes in the URL (a website address).
Check that the website is secure before paying for any service or providing your card details: HTTPS, a padlock and no spelling mistakes in the URL (a website address).- Most scammers go after their victims through spam emails that either include phishing messages or include some sort of malware. So be cautious and never click links in emails or messages (on other platforms) that come from unknown addresses or look weird (e.g. you won a lottery that you never played or got a package waiting for you, though you didn’t buy anything, or you inherit millions, or that you need to renovate your subscription to a service that you know you didn’t use, or that your account is blocked etc.).
- Keep your devices safe: keep your computer and software updated (both Microsoft and Apple regularly release updates for their operating systems, so don’t ignore them once they are available for your computer); use an antivirus programme on your computer and mobile and keep it up to date.
Regarding online booking, let’s go over some additional practical steps to protect you from fraud:
- Try booking directly through the hotel´s official website. You already know the most important elements to look for in a web page to make sure it’s not a fake twin: logo, URL address, contact details (make sure that the address and phone number are real, and the e-mail address has its own domain, e.g. info@com and not info@gmail.com; clearly defined terms and conditions).
- Choose a reputable company if you choose a third-party booking site because it is the best way to get an offer or combine your needs. Further on in this unit, we will provide you with a list of websites with good reputations that you can trust.
- Be careful when paying. Many hotels won’t charge you in advance (although this depends on the type of booking and cancellation policy), but you will be requested for the card details, and you will have to pay every time you buy any kind of ticket online. Remember that you should not pay directly from a bank account or make a bank transfer (including Bizum as this works like a transfer). If there is a possibility to pay with PayPal, that is the safest way. If not, it is better to use a credit card (they usually have extra protection against fraud) rather than a debit card.
- Often, when we are on the go (be it at the airport, train station or hotel), we often use a wi-fi service on offer. This is very convenient, but avoid using public Wi-Fi services for transactions. Nowadays, there are no extra charges for roaming services within EU countries, so you can use your phone as you would in your home country without paying extra on top of your contract tariff. Unfortunately, this only applies to the EU. In all other countries, you may be charged high fees for using your phone while roaming and be obliged to connect to a public Wi-Fi. In this case, you can get extra protection by turning on VPN (see definition above), which gives you a private gateway for your network connection. However, you need to trust your VPN service provider. (If you are interested in VPN and want to know how to install and switch it on, check this article: https://www.xataka.com/basics/que-es-una-conexion-vpn-para-que-sirve-y-que-ventajas-tiene ).
- After making a booking, ensure you receive an email confirmation of your booking and/or ticket you purchased. Reputable websites usually have this process automated.
- The last piece of advice: trust your intuition. If some deals seem too good to be true, they usually are.
